Why Executive Protection Professionals Need to Embrace the Internet of Things – for Better, for Worse – and for Good
Sign up to receive our blog posts in your inbox.
There’s a lot of talk about the Internet of Things (IoT). The IoT is growing rapidly in size and complexity. It’s expanding into more and more types of devices and applications, and it’s getting smarter. It’s disrupting all kinds of industries – for better, for worse and for good. The IoT is not going away, and the pace of change will skyrocket in the coming years.
It will also have an impact on the executive protection industry, too. Even though executive protection professionals are not IT experts, understanding the security implications of the IoT is no longer an option. It’s a necessity that we have to deal with today, and it will only become more critical tomorrow.
The security playing field is changing as more devices become connected and more data from these things becomes available. We ignore these changes at our peril – and that of the principals we protect.
In this blog, we examine some of the issues surrounding IoT and protective security. The risks and vulnerabilities caused by the IoT to our clients’ safety, productivity and privacy are real, critical and growing, and they must be considered as we design and implement comprehensive security programs. At the same time, the IoT also offers protective security professionals a range of opportunities that were not possible a few years ago.
What is the Internet of Things?
Before we get started, let’s make sure we’re talking about the same thing here. There are a lot of definitions of the IoT, but most of them touch on four key aspects:
- Things and devices (e.g., sensors, cameras, actuators, electronics, software, vehicles, buildings, computers, cloud computing facilities)
- That connect to each other and other things via the internet
- To collect and exchange data – and increasingly – to process and analyze data
The IoT is still very much related to industrial rather than consumer spending (think manufacturing, utilities, transportation and logistics). As the Boston Consulting Group points out in a recent article, it’s important to understand that there is no single internet of things. If you follow the money, it’s the many different and distinct use cases that are driving the overall market growth. The bulk of investments go to use cases like predictive maintenance, self-optimizing production and automated inventory management – not to fun things like smart watches and clever refrigerators. This, too, will change.
Why should executive protection professionals care about the IoT?
The IoT brings with it a new range of threats to our principals’ security and privacy.
Let’s consider security first. Anyone with intent, smarts and a SHODAN account can quickly target SCADA and other industrial control devices, webcams, printers, toasters and a host of other gizmos – maybe even one near you or your principal. You don’t even need smarts and your own account – you can just hire someone to do the dirty work for you.
The IoT opens all kinds of other doors that can threaten the principal’s security, too. This can range from hacking a car’s steering and brakes to fiddling with a residential alarm system. It can include surveillance of the principal to make his or her locations at given places more predictable. It could be a direct drone attack.
The threat to privacy is no less real. The stakes can be high, the barriers quite low. Presumably innocuous appliances can, relatively simply, be repurposed to become surveillance devices. Personal and corporate secrets can be captured and exploited for any number of reasons: hacking and cyberstalking can be motivated by greed, politics, revenge or even an adolescent sense of adventure.
Hardly a news cycle goes by these days without a report of new, unexpected IoT security breaches. Here are just a few:
- Jeep recalled more than a million vehicles after a staged hack revealed glaring security holes accessible via the onboard entertainment system.
- Hackers gained access to 800,000 customer credentials and more than two million voice recordings connected to an IoT teddy bear.
- The FDA issued a warning that some pacemakers can be hacked, not only to steal data but to run down batteries or change heartbeats.
- Hackers initiated a massive Distributed Denial of Service Attack (DDoS) on Dyn, an internet infrastructure company that hosts websites such as Netflix and PayPal, using the Mirai bot and hacked CCTV cameras and digital video recorders.
There are three trends that are making executive protection professionals think more about the IoT:
1. Exponential growth: The tremendous growth in volume, type and complexity of connected things means there are more devices available to hack, hijack or otherwise misuse.
The IDC’s 2016 Digital Universe Update estimated that the number of connected devices will skyrocket from about 20 billion now to 30 billion in 2020 – and to a staggering 80 billion in 2025. Pretty much everything to which we assign any value will be connected.
The ubiquity and sheer size of the IoT mean that executive protection professionals have no choice but to include it in security considerations. Access to the principal has multiplied in new ways, opening a heretofore unseen range of new vulnerabilities and potential points of failure. If in the past there were ten doors to protect, both literally and figuratively, there are now hundreds and soon thousands. Each door is of varying strength and security, and the safeguarding of each door will require constant vigilance and updates to let in the people that are authorized and keep out the people that are not.
2. Lax security standards: The number of devices connected to the internet is growing exponentially. The security of these devices is not, however.
Commoditization of components and bandwidth are one reason: the bits and bytes that enable the IoT are forever getting cheaper. As market factors drive down costs, security easily gets lost in the competitive shuffle. Consumers are more concerned with price and features than they are with data privacy. While it’s quite likely that a piece of 100-dollar kit – say, a “security camera” – could stay hooked up to the internet for years, it’s quite unlikely that its designer or manufacturer opted for the most secure hardware and software. It’s even less likely that the gear will get regular security updates – if any at all.
The extremely heterogeneous nature of the IoT exacerbates a plethora of cyber security issues. There are so many different “things” with so many different hardware profiles used in so many different ways that standardization is elusive. Network security is complicated by the varied communication protocols of so many device types. Data encryption, similarly, is trickier when data flows across a wide range of device types. Authentication is different than what we normally do when we log onto a laptop or open our phones (e.g., type in a password or do a fingerprint scan); many IoT interactions and authentication processes don’t involve humans at all.
The lack of national, international and commonly applied cyber security standards is a real problem. Security is not “built-in” to most IoT devices; it’s tacked on after the design process has been completed. The International Organization for Standards’ committee on consumer policy (ISO/COPOLCO) is working to change this, but we are far from having any standards that do for cyber security what other ISO standards do for basic product safety. Given the speed of technological change, it will, in any case, be difficult to maintain the relevance of standards as innovation surges ahead.
The IoT is moving from industrial applications, where enterprise security solutions are taken more seriously, to consumer applications where security is generally more relaxed. The shift from industrial to consumer focus will probably mean that IoT security will continue to be lax, unlegislated and unreliable – at least for the foreseeable future. The huge number of startups and innovations with little oversight or professional security expertise will exacerbate this trend.
3. The rapid proliferation of AI: Increasingly, we live in a world where we leave digital traces no matter what we do or where we go. As the streams of data coursing through the IoT surge to an estimated 2 zettabytes in 2025, the role of data analysis – and thus of artificial intelligence (AI) will grow by leaps and bounds. To put things into perspective, two zettabytes are a 2 followed by 21 zeros, or 2 trillion gigabytes of data. That’s a lot of valuable resources to leave unmined.
Currently, precious little of the internet’s and the IoT’s tsunamis of digital data are ever analyzed. AI will change that. Let’s include machine learning, data mining and predictive modeling here, too. If Data is giving rise to a new economy, as The Economist recently reported, AI is what’s going to make sense of it all. AI will gradually change the landscape of security in our world, too. Not as quickly as other industries, for sure, but just as relentlessly.
Facial recognition technology powered by AI will continue to improve, for example, as will AI’s growing capacity to provide other kinds of understanding. Like other tools, AI’s ability to find sense in huge amounts of available data can be used for good purposes or bad. Wherever the good guys can use IoT and AI to discern patterns, make more accurate predictions and discover new insights, the bad guys can, too.
The IoT and big data streams will create future opportunities for executive protection professionals
Like the clients and companies, we serve, executive protection is a professional service that is increasingly tech-enabled. All industries, including ours, have to realize that staying in the 20th century is not an option: the tech evolution is happening and will continue to unfold in new ways.
Just as the military uses IoT tech and data to boost man-machine symbiosis, so will EP.
According to Lockheed Martin’s Steve Froelich, Director of Operational Command & Control, the OODA decision-making cycle (Observe-Orient-Decide-Act) will span more domains – and include ever-larger amounts of sensor data – to enable people, enhanced by machines, to make better decisions, faster. Froelich cites the following battlefield examples:
- “Advances in data fusion and machine to machine automation make data accessible, understandable, and conditioned so that automated tools can effectively use the data for rapid decision-making.
- Integrating predictive intelligence helps intelligence analysts better understand seemingly disparate relationships by making rapid connections between people, places, and things.
- Merging the command and control (C2) operational environment with the intelligence, surveillance and reconnaissance (ISR) environment helps to improve automation of the intelligence cycle by giving commanders a view of everything that is happening in the battlespace. The convergence of the C2 and ISR environments will provide the ability to probabilistically predict likely events in the future.”
Admittedly, we in the field of EP are nowhere near the sophistication of the US military. But history shows that technology that starts in the military often trickles down into the civil sector. We believe that some of the same processes that Froelich describes will take place as EP teams begin to take advantage of the IoT and big data.
Whether the EP team is running a professional service business as an external specialist partner or are part of the corporate staff, the IoT and the increase in available data will be a boon as well as a bane. Throughout the EP org chart, which itself will change as technological developments occur, the IoT will create new opportunities across a number of use cases and business objectives that are already priorities in our industry, such as:
- Improving the quality of protective security programs
- Integrating intelligence analysis into executive protection
- Increasing protective detail efficiency to reduce costs
A new EP org chart for the IoT era
As technological advances continue to disrupt both sides of the threat/mitigation equation, executive protection teams will have to transform to keep up with the changes. New areas of expertise will be included under the umbrella of EP management and new forms of collaboration will become more common.
We believe the future organizational chart for executive protection departments will look something like this:
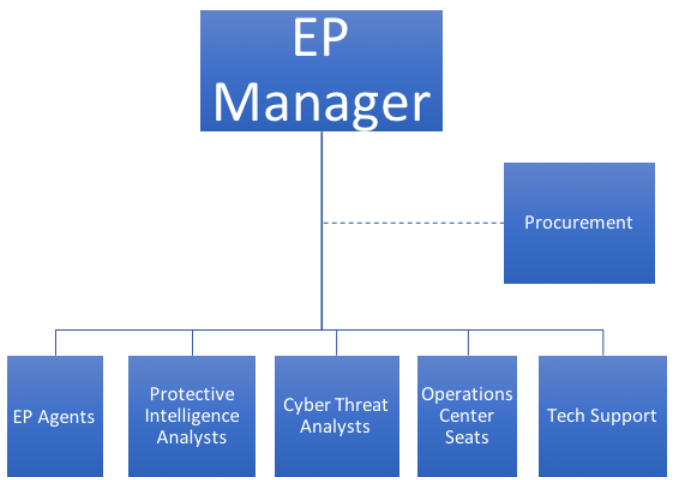
EP Agents (EPAs) will still report to the EP Manager, whose role will expand in several ways.
The EP Manager will work more closely with Protective Intelligence Analysts (PIAs) and Cyber Threat Analysts (CTAs) to proactively identify and analyze the new types of risk to the principal ushered in by the IoT. Both will work together to monitor, analyze and report on risks, threats and other developments that may impact the principal’s safety, privacy, productivity or reputation.
PIAs proactively research and report on a host of issues that are pertinent to the principal’s security whether at home, on the corporate campus or while on the road. These include ongoing tracking and ad hoc investigations of persons and groups of interest (POIs and GOIs), as well as personalized travel risk assessments that go beyond general destination information to dig into what might threaten the principal at a specific time and place.
CTAs proactively hunt and report on potential and emerging cyber threats to the principal. Such efforts go beyond corporate-wide procedures, and instead narrow in on threats that are specific to the principal and others in the C-suite. CTAs use a variety of tools and routines – and large amounts of data – to gather intelligence about personal cyber risks and to develop appropriate countermeasures.
The EP Manager will also oversee one or more seats in the organization’s security operations center. It is here that intelligence – including that provided by EPAs, PIAs and CTAs – together with surveillance input from IoT and other sources will enable better command and control decisions.
Finally, the EP manager will work closely with tech support experts to evaluate, implement and manage new security technologies as they emerge. Tech is an integral and inevitable part of any world-class security program, and the EP manager must integrate tech in strategic security planning – and use tech as a force multiplier.
EP agents as centaurs?
We don’t expect EP agents to take too many plays from the playbook of Garry Kasparov, the chess grandmaster whose pioneering battles with IBM’s Deep Blue computer became the stuff of legend. However, EP professionals can learn from his experience when it comes to combining human and artificial intelligence.
Kasparov came back from his 1997 defeat to Big Blue to develop a new type of chess: “advanced chess”, which combines people and machines working in close cooperation. The computers had access to moves from millions of games, but the winner of the matches still needed to come up with a good idea.
Also known as “centaur” chess, the game has led Kasparov and others to some startling insights in combining human and computer intelligence. As Kasparov writes in his insightful NYT review of Chess Metaphors: Artificial Intelligence and the Human Mind, interesting things start to happen when we move beyond the simple dichotomy of “people vs computer”, and let them play as partners instead.
Kasparov describes a tournament that included grandmasters and amateurs competing for a cash prize with the help of computers. At first, he writes, results were predictable. Supercomputers similar to Deep Blue were “no match for a grandmaster using a relatively weak laptop.” But Kasparov was surprised by the eventual outcome of the tournament, which was won by a couple of amateur chess players who used three computers at once. Their victory was due to neither their skill at chess nor the computational strength of their devices, says Kasparov, but to the way they “coached” their computers to outdo stronger players and more powerful computers.
Kasparov’s conclusion is something we in EP should heed:
“Weak human + machine + better process was superior to a strong computer alone and, more remarkably, superior to a strong human + machine + inferior process.”
Don’t forget the basics
Like Kasparov’s chess centaurs, we EP professionals can also up our game with smart people and smart machines, but we get the very best results when we use smart procedures. Let’s think about this as we approach the new era of IoT and EP.
As we embrace the IoT and other technological developments, let’s not forget the basics of EP, the classical realm of physical threats. After all, it’s important to remember how to do the job both with and without technology.









